Which of the Following Best Describes an Email Security Gateway
44 Which one fo the following best describes phishing. The attack works as follows.
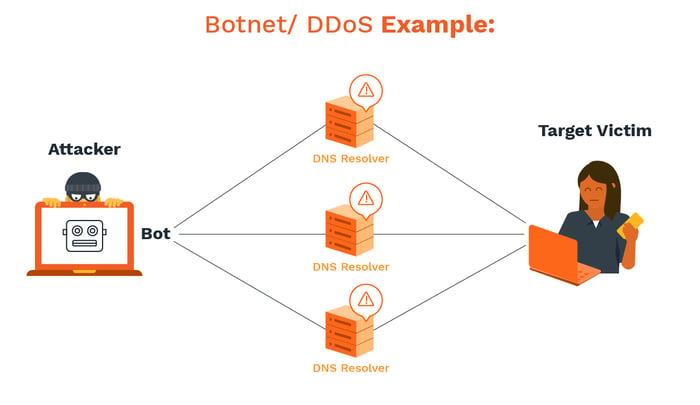
The Ultimate Guide To Email Security And Best Practices
A proxy server is a computer that acts as a gateway between a users computer and the Internet.
. A gateway with only one exit path per instance of a processd. All Layer 2 switches should leverage Active Directory tor authentication. Question 36.
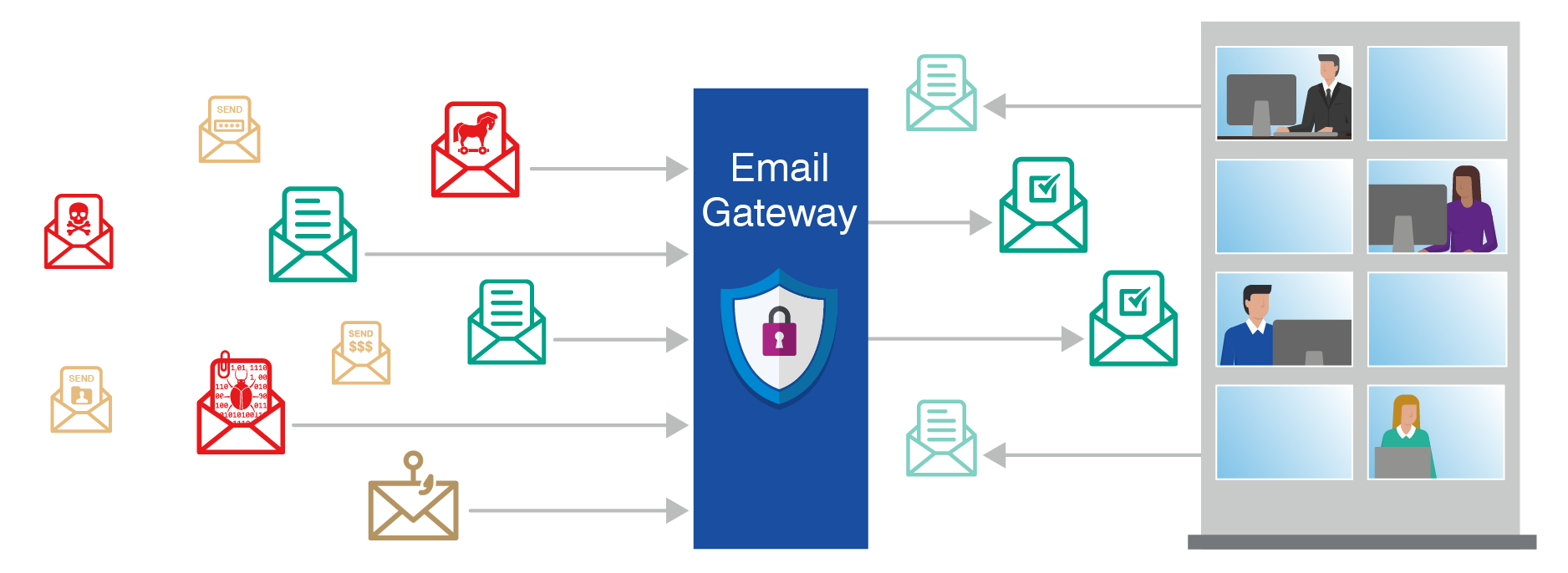
A security administrator would like to increase the security of the companys email communication. Which of the following is. An email gateway scans and processes all incoming and outgoing email and makes sure that threats are not allowed in.
Simple Mail Transfer Protocol SMTP specifies how messages are transmitted. Which of the following best describes an exclusive gatewaya. Only the global administrator can manage groups across tenants and assign other administrator roles.
He is using an LMHOST file which contains the hostname and IP address of the new server. The user in unable to authenticate because they are outside of the organizations mobile geofencing configuration. By this the client computer can establish indirect network connection to.
Simple Mail Terminal Protocol D. The security team at a large corporation is helping the payment-processing team to prepare for a regulatory compliance audit and meet the following objectives. Because attacks are increasingly sophisticated standard security measures such as blocking known bad file attachments are no longer.
A security audit performed on the internal network of an organization by the network administration is also known as ___________. A gateway where all exit paths are taken for each instance of a processe. A subject Abbrivation of SMTP is.
The server that he cannot remotely access to is located on. Email -- but not email security -- protocols. CompTIA Security Exam 2021.
Email Security provides protection against spam spoofing and viruses. UTC 04052018 030915809 AV Gateway Alert 13612792171 80 - 10161014 60818 Gateway Anti-Virus Alert. We can control network traffic to resources in a virtual network using a network security group.
Limit the scope of the audit to only devices used by the payment-processing team for activities directly impacted. An email directing the recipient to enter personal details on a fake website An email warning the recipient of a computer virus threat An email advertyising a department store An unwanted email that installs a virus on the recipeints computer A 45 What is WPA. The only recent log entry regarding the users computer is the following.
Do you want to create a DMZ for these two servers. They scan the network to determine the IP addresses of at least two devices. Firewall management lets you monitor and configure Sophos Firewall devices that you connect to Sophos Central.
The laptop is still configured to connect to an international mobile network operator. The attacker must have access to the network. This prevents most attacks from reaching their intended recipients which in turn reduces the number of successful compromises of hosts user credentials and sensitive data.
A white-hat hacker is a good guy who uses his skills for defensive purposes. Your company has a connection to the Internet that allows users to access the Internet you also have a Web server and an email server that you want to make available to the Internet users. Sophos Web Gateway protects your network against risky or inappropriate web browsing.
The only gateway in a BPMN diagramb. It is therefore imperative that every organizations security strategy include a robust email security solution. One of the first best practices that organizations should put into effect is implementing a secure email gateway.
Reduce the number of potential findings by the auditors. A subject B cc C to D contents. The following control how email is transmitted formatted and retrieved.
SpamTitan is built on a powerful spam filtering platform with a market leading catch rate of 9999 and a false positive rate of 00003. In the Email Following term describes the contents of the message. Which of the following BEST describes the environment that the network administrator will.
SpamTitan is a leading secure email gateway platform that provides comprehensive protection against email threats including spam malware ransomware and phishing attacks. The proxy server is also called application level gateway. Simple Mail Transport Protocol C.
During an investigation an analyst determines the system is sending the users email address and a ten-digit number to an IP address once a day. A gateway that does not connect to message flowsc. Az network nsg create is used to create a network security group.
Simple Mail Transition Protocol Answer A Select correct stands of XML. None of the above. Solutions for Chapter 2B Problem 14MCQ.
CompTIA JK0-801 A Networking PC Hardware Practice Exam Set 6. A security engineer needs to Implement the following requirements. A with external access.
Simple Mail Transfer Protocol B. Michael is a system administrator who is troubleshooting an issue with remotely accessing a new server on the local area network. All Layer 2 switches should use local fallback authentication If Active Directory Is offline.
What is ARP Spoofing ARP Poisoning An ARP spoofing also known as ARP poisoning is a Man in the Middle MitM attack that allows attackers to intercept communication between network devices. All Layer 2 switches are not the same and are manufactured by several vendors. Wi-fi protected access wired.
All email security gateways have the ability to quarantine or block email that contains detected malware phishing attacks spam as well as other malicious content. Basic insecure email depends on just a handful of protocols. Question 6.
It is important to note that these are not email security protocols. An end user reports a computer has been acting slower than normal for a few weeks. Whether its sophisticated nation-state attacks targeted phishing schemes business email compromise or a ransomware attacks such attacks are on the rise at an alarming rate and are also increasing in their sophistication.

What Is Email Security Meaning Best Practices More Proofpoint Uk

What Is Email Security Definition Benefits Examples Best Practices Toolbox It Security

Comments
Post a Comment